Intro to Packet Sniffing: Catching Fraud With Wireshark

The enterprise world is just as susceptible to fraud as consumers. However, the word ‘fraud’ can be a bit of a misnomer. When we typically think of fraud, we think of identity theft or stolen credit cards. Nevertheless, fraud comes in all shapes and sizes. One type of fraud that affects the business world is hijacked networks, and it's more common than you might think. We'll delve into how Wireshark can be utilized to detect such frauds.
While this introduction to packet sniffing brings valuable perspectives for IT pros, it doesn't cover everything. If you need a more robust network and network diagnostics class, check out CBT Nuggets CCNA online training.
What is Packet Sniffing?
Packet sniffing is the act of inspecting network packets as they flow through a network. Imagine it like a drug-sniffing dog that walks around in the airport sniffing bags — except this one is looking for fraud. While many enterprise-grade networking hardware include packet sniffing functions as diagnostic tools, IT pros also have access to other applications, like Wireshark, that perform packet sniffing from client devices. These applications are used for both security auditing and diagnostic purposes.
What is Wireshark?
Wireshark is a popular tool within the IT space. It’s a free application that can run on most hardware with a network connection. Wireshark is also included in some routers and routing software, like PFSense.
Wireshark is a simple tool to use. It starts by intercepting packets coming and going from the network interface of the device running it and spits the information within the packet into a log. That information includes information in the headers and the body of the packet that you can filter and compile into reports. Think of Wireshark as a real-time data mining tool.
It should be noted that if packets are encrypted, the information Wireshark provides is limited. More advanced packet sniffing techniques are required to view encrypted data. But this doesn’t mean that Wireshark isn’t helpful.
Why is Wireshark So Useful?
Whether network traffic is encrypted or not, Wireshark can be incredibly useful for discovering issues. A lot of information can be gathered from metadata itself. In fact, this is one of the reasons a big stink was made in the IT and privacy communities after the Edward Snowden revelations.
Wireshark can tell us where data comes and goes from a device and how often it’s sent. It can also tell us the size of the packets. Though this information is basic, Wireshark can provide much more data.
Catching Network Problems With Wireshark
End-users will always try to bypass IT to install applications they deem necessary to do their job. After all, no one likes submitting help-desk tickets. While IT can lock down devices, preventing portable applications or browser plug-ins is challenging.
We’ve all heard of browser plugins and websites using hijacked machines for crypto mining. Crypto mining is easy to detect, though, through CPU spikes. However, there is a much more nefarious problem that is difficult to detect: proxy services.
An entire cottage industry in the black market sells hijacked network access to bad actors. These services are like VPN products like ExpressVPN, except they are designed to make internet traffic appear as if it’s coming from a reputable source. This process allows fraudsters to mask their location and bypass security mechanisms like captchas or VPN checks.
Corporate networks are the cream of the crop for these services. Hijacked corporate networks let bad actors pass themselves off as an employee of a business from a digital forensics standpoint. Finding infected machines on a corporate network can be a nightmare, too.
How are Corporate Networks Hijacked?
Backdoor proxy services can be installed with third-party applications. However, this intrusion method isn’t as widely used anymore. Endpoint security suites have become very sophisticated and can detect locally installed malware quickly.
Another infection vector has become more prevalent: browser plugins. Bad actors are creating browser plugins that pipe network traffic through plugins installed in the browser to the outside world. These plugins use public proxy services, like Cloudflare, to hide the connections between these browser plugins and their piped connections. Traffic piped through these fraudulent proxy services is often scattered between hijacked clients, much like a TOR connection, making them even more challenging to catch.
Catching Fraud With Wireshark
Let’s say that an end-user submits a help ticket stating that their network connection is slow. After preliminary diagnostics, the IT tech can’t find anything wrong. Yet, they can replicate the issue just by using the computer. All websites on it take forever to load.
A common solution is to re-image the end user’s device. This process can take hours, however. It’s not a solution that anyone enjoys.
This is where Wireshark shines. It’s a great diagnostic tool for monitoring everything happening on all seven network layers in the OSI model. IT techs don’t need to be a Wireshark expert in this scenario, either.
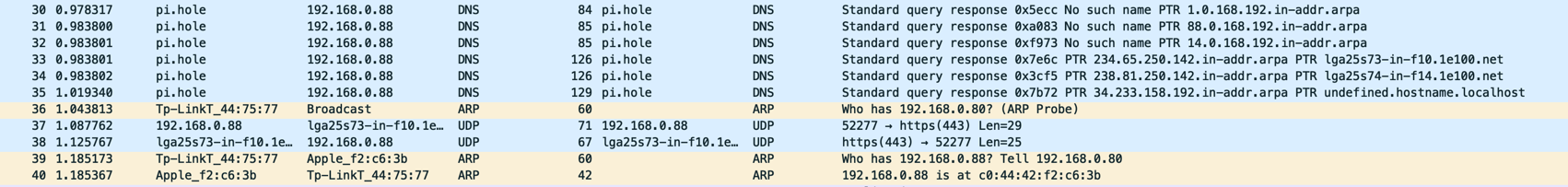
Let’s look at an example of a Wireshark log:
There are a couple of interesting entries in that image. First, that computer is using PiHole for DNS resolution. Second, it is an Apple device. We can tell this from line 48, where the Apple device is responding to a broadcast request.
Wireshark can be used the same way on an end user’s machine to see where data is coming and going. By simply monitoring the Wireshark logs, IT techs can see whether a rogue application is sending malicious data from a computer. From there, it’s a simple, standard diagnostic process of narrowing down the problematic app.
Learn More About Packet Sniffing
Wireshark can be used for so much more, and it’s a tool you need to know if you want to earn the CCNA. To delve deeper into acquiring CCNA certification, consider taking Jeremy Cioara’s CCNA online training.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.