What is Port 3389?
by Colin Cohen | Published on October 20, 2023

Port 3389 is dedicated to Remote Desktop Protocol (RDP), which allows users to access and control their desktop computer remotely.
Client and Remote Server Communications Over Port 3389
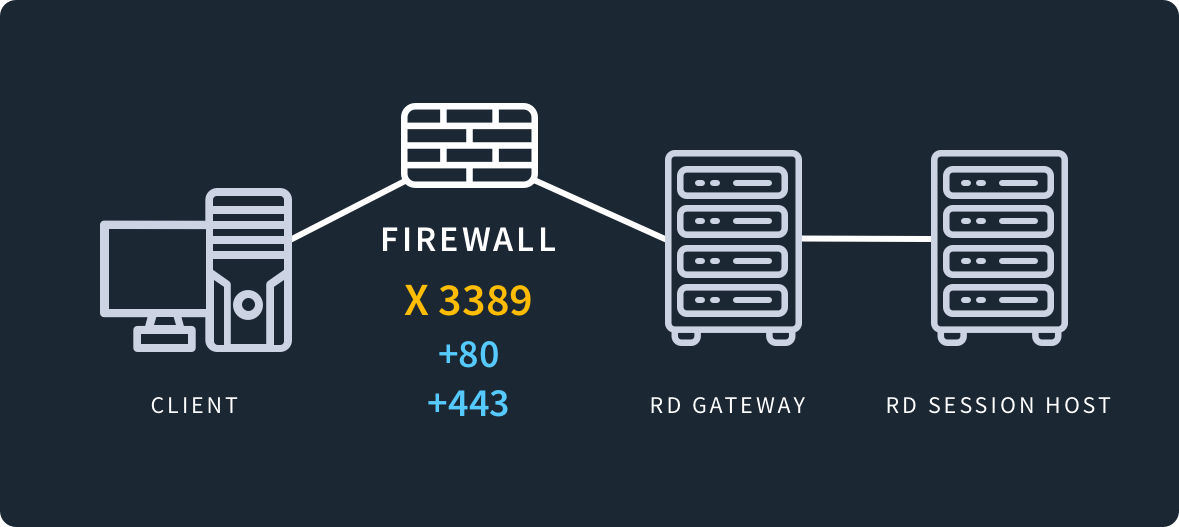
If a user needs to access a remote Windows computer, it's possible to do so using the Remote Desktop Protocol (RDP) via port 3389. Leveraging RDP allows the user to perform the same functions on a local desktop or server remotely — even thousands of miles away — just as if they were sitting at the console itself. Once connected to the remote computer, it’s as if the connected device actually becomes the remote computer, regardless of what operating system it is running.
Though RDP was created by Microsoft to use for remote connection originally with Windows operating systems, it's since evolved to work with Mac OS, Linux, and Unix systems via third party packages.
Does RDP Use Port 80?
Because there are some vulnerabilities associated with port 3389, some network admins may opt to block the use of the port number. To bypass this, it's possible to set up RDP through an SSH tunnel over port 80, which is dedicated to standard HTTP traffic (and therefore less of a security risk).
What is RDP Port 3389 Used For?
You use RDP over port 3389 to make remote connections to desktop computers, after which you essentially take control of them. For instance, if an employee needs to work remotely and cannot bring their desktop computer with them, they may leverage RDP to access the local files that are stored on their desktop via another device.
While many companies have transitioned to the cloud, some may not have migrated or are unable to for security requirements or regulatory controls. This is where RDP comes into play. RDP allows the user to use remote desktop software to access their physical desktop computer and the files and applications that are saved locally on that desktop.
How to Use Remote Desktop Connection and Control
To use RDP, you must enable it through the settings of the desktop computer that you want to provide access. Clients can then set up a connection to the desktop through Microsoft’s Remote Desktop Connection tool. Once connected to the remote computer, your screen will mimic the desktop (and its local files and applications), allowing you to use the remote device as if you were sitting right in front of it.
For more information about how to use Remote Desktop Connection, check out this tutorial on remote access methods from Keith Barker. Keith is a twice-certified CCIE holder who specializes in networking and security. The latest Network+ online training has additional information about RDP and other ports and protocols, as well.
Features of RDP
While there are certainly risks to using Remote Desktop Protocol (RDP) and port 3389, it's impossible to deny the features of using RDP. The main functions of RDP include:
The ability to remotely control another computer.
The ability to share resources between the local and remote computers.
The use of encryption enables secure communication between the computers.
Difference Between RDP Port 3389 and 443
Speaking of security concerns, sometimes you cannot use port 3389 on a particular network because it has been blocked by a network administrator. To get around this, you can redirect RDP traffic through port 443, which is dedicated to standard HTTPS traffic.
Port 3389 Vulnerabilities
Having port 3389 open in your firewall can expose you to various security threats, such as man-in-the-middle attacks. Port 3389 is the default RDP port, making it an attractive target for hackers who know about its vulnerabilities. Never leave port 3389 exposed to the public Internet unless you cannot avoid it. In those cases, consider using a different port than 3389.
As remote desktop access is often a necessary risk, be sure to proactively protect against the following vulnerabilities that using port 3398 can expose your networks to.
1. RDP 3389 Gives a Direct Pathway Into a Computer
Leaving port 3389 exposed to the public Internet can allow an attacker to access and control the computer. This can expose sensitive information and allow the installation of malware, such as ransomware.
Because of this, many organizations will block port 3389 in their firewall and only allow the use of RDP through a VPN.
2. Avoid Weak Passwords When Using TCP Port 3389
It is not uncommon for attackers to use brute-force methods on computers that have port 3389 open. Using tools such as nmap, they can enumerate common usernames and passwords and attempt to use them on the target computer.
For this reason, it is important to avoid weak credentials on computers that allow RDP access. You can do this by creating security policies that will prevent their creation.
3. Port 3389 Vulnerability to Man-in-the-Middle Attacks
Because RDP clients do not validate an RDP server’s identity when setting up encryption, an attacker who intercepts traffic from an RDP server can set up the encryption itself. This allows the attacker the potential to obtain sensitive information what's called a "man-in-the-middle attack." Using an encryption-based Internet security protocol like SSL can protect against this kind of vulnerability.
Using TCP Port 3389
In Windows, you can change the RDP port from 3389 to another and check if this port is open.
How to Change RDP Port Number in Windows 10
To change the RDP port number from 3389 to another in Windows, do the following:
Run regedit to open the registry editor.
Go to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp.
Find the PortNumber and click Edit > Modify and then click Decimal.
Enter the new port number and click OK.
Exit the registry editor and restart your computer.
How to Check if Port 3389 is Open
To determine if port 3389 is open on your computer, run the following command from the Command Prompt:
netstat -aon
The output of this command will indicate if port 3389 is in a LISTENING state, which means it is open.
Alternatives to Port 3389 RDP
Given the risks, it's no surprise that there are a few other options for remote access that do not require the use of RDP port 3389. Alternatives to using RDP include the following:
Virtual Network Computing (VNC): Similar to RDP, VNC is a protocol used for remote computer administration in a graphical environment. VNC is a platform-independent and uses the remote frame buffer protocol.
Secure Socket Shell (SSH) port forwarding: SSH port forwarding is a convenient and secure way to allow remote desktop connections. You can use SSH port forwarding to encrypt the connection from one host to another (even when using public WiFi).
Virtual Network Computing (VNC) vs. RDP Port 3389
Virtual Network Computing (VNC) is another means of remotely connecting to a computer. Unlike RDP, which is Windows-specific, VNC is platform-independent. It does support streaming graphical user interfaces (GUI).
On the other hand, RDP is generally more performant than VNC. So, RDP will likely be a better choice over VNC if you want to connect to a Windows desktop remotely.
Secure Socket Shell (SSH) vs. RDP Port 3389
You can also remotely connect to a computer using SSH. The main difference between RDP and SSH is that SSH, unlike RDP, has no support for graphical user interfaces (GUI). So, it’s more geared to connecting to Unix-like operating systems, such as Linux.
Key Takeaways for Understanding Port 3389
Port 3389 is used to facilitate remote access to Windows computers through the Remote Desktop Protocol (RDP). This connection method allows users to operate a remote desktop or server as if they were physically present, regardless of location. Originally designed for Windows, RDP has expanded its horizons, and is now compatible with Mac OS, Linux, and Unix systems via third-party solutions.
Using RDP port 3389 does include some security risks that you should keep in mind. Namely, leaving the RDP port open to the Internet can allow attackers access to the network. Consider using an encrypted SSH, a VNC protocol, or redirect RDP traffic through port 443 instead.