What is Port 22?
by Colin Cohen | Published on October 20, 2023

Port 22 is dedicated to Secure Shell (SSH), which allows you to securely connect to a remote device and issue commands as if you were in front of it.
What is a Shell?
A shell is a program that lets you perform operating system commands on a device, typically through a command-line interface (CLI).
Understanding Secure Shell
SSH was developed to replace Telnet, which functions much like SSH but without providing a secure environment. SSH adds various features to overcome Telnet’s limitations by allowing you to connect securely to a remote device over an unsecured network.
To use SSH, enter the following command from a terminal or a command prompt:
ssh [username]@[host]
username is the username on the remote host that you want to logon as, and host is the hostname or IP address of the remote device.
Upon issuing the above command, the remote device will request your password and then authenticate you.
Which Protocol Uses Port 22?
SSH protocol consists of three separate protocols, which include:
A transport layer protocol, which handles server authentication and data integrity
A user authentication protocol, which handles user authentication
A communication protocol, which manages encrypted tunneling
Port 22 vs Port 162
While port 22 is dedicated to connecting to remote devices using SSH, port 162 is used for sending logging and management data to remote monitoring applications using Simple Network Management Protocol (SNMP).
TCP Port 22 vs Port 443
You use port 22 for SSH to make secure connections to remote devices and run commands. You use port 443, on the other hand, for securely transmitting sensitive data such as credit card numbers in a web browser using Secure Socket Layer (SSL) over HTTPS.
You can also use port 443 for SSH tunneling if, for some reason, you cannot use port 22.
What is Port 22 Used For?
System administrators and others who need command-line access to remote devices use SSH over port 22 to manage these devices.
Port 22 Gives Secure Remote Access to Devices
You cannot always physically be at a device you need to manage. By using SSH over port 22, you can remotely access and control any device anywhere in the world as if it were your own device, and you can do this in a secure manner.
Who Needs Command-Line Remote Administration?
System administrators and similar professionals often have to manage devices located remotely, which could be at another location within the organization or in the cloud. These people will typically use command-line tools to do this, especially when managing devices running Unix-like operating systems such as Linux.
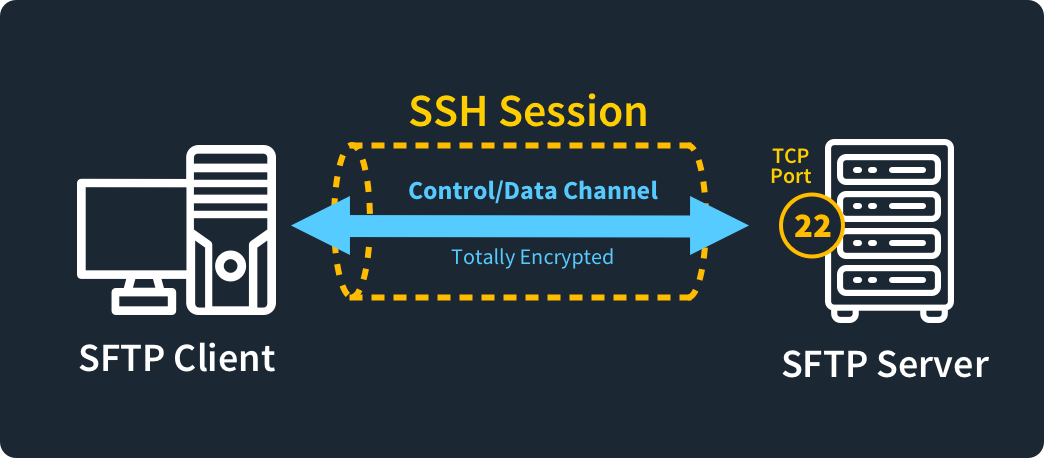
How Does TCP Port 22 Enable Secure File Transfer?
If you need to transfer files between devices securely, you can use SSH File Transfer Protocol (SFTP) over port 22. SFTP works much like FTP, only it does it far more securely.
RELATED: What Are TCP Ports and Why Are They Important?
Using the Default SSH Port
While the default port for SSH is 22, you can block it in your firewall and instead only allow SSH access through encrypted tunnels. You can also switch SSH to another port.
Creating Encrypted Tunnels with SSH Port 22
You can use encrypted tunnels with SSH if you need to use port forwarding to connect to an SSH server. This is useful, for example, if a firewall blocks the default SSH port 22.
VPN Solutions That Depend on Port 22
Many VPN solutions will block port 22. When this happens, you must use tunneling to connect to an SSH server, also known as port forwarding. With tunneling, you will use a different port for SSH, like a port that the VPN won’t block such as port 443.
How to Make Sure TCP Port 22 is Secure
Hackers often target port 22 because they could potentially do unlimited damage if they can log onto a remote device. Because of the risk, many organizations will turn off port 22 and instead use a random port for SSH, somewhere between 1024 and 65535.
Understanding how to keep port 22 secure is critical for keeping your networks safe from intruders. Here are a few ways to mitigate the risks of port 22.
1. Learn to Spot Misconfigurations and Weak Authentication
Often, default SSH server implementations will allow logins as the root user. Because root has unlimited control over the remote device, you should disable these types of logins.
Another common SSH-related misconfiguration is when you only want to allow SFTP without shell access. To properly do this, you must disable TTY access, as well as port forwarding and tunneling.
You also have to ensure that you set up security policies within your organization that prevent the use of weak credentials. There are several ways to make sure members of your organization are creating more secure passwords, and can help end users stay safe.
2. Block Vulnerable Ports Like Port 22 on Your Firewall
Because port 22 is so notorious for risks, many opt to block it from use altogether. Once you've enabled SSH tunneling, you can block port 22 in your firewall.
Examples of Port 22 Conflicts
Only one process can listen to port 22 (or any port, for that matter) at a particular time. If another process or server uses port 22, you must stop it before running your SSH server.
To determine if port 22 is available on your device, run the following command from your terminal:
netstat -aon
The output of this command will indicate if port 22 is available or in conflict with another process.
Can You Run an SSH Server and Web Server Simultaneously?
If, for some reason, you cannot run SSH over port 22 (if this port is blocked, for instance), you may be able to tunnel over TLS on port 443 using your web server.
Key Takeaways for Using Port 22
Port 22 is associated with the SSH (Secure Shell) protocol, which is used to securely connect to a remote device and issue commands just like you would on your own device. This default port does have its vulnerabilities, though: port 22 a popular target for brute force attacks and unauthorized access attempts. To keep port 22 more secure and ensure a more secure remote access experience, you should disable the root login, utilize strong passwords, and enable key-based authentication.