Symmetric vs. Asymmetric Encryption: How They Work

Cryptography has been around since long before computing. Encryption has been used by governments and armies for thousands of years to protect important messages. Today, advanced encryption is a critical part of any secure IT infrastructure.
The idea is to send information from one computer to another, but scramble it so that only those with proper permission can see it. There are two types of encryption: symmetric and asymmetric.
Let's explore both types of encryption, so you can learn best when to use one or the other. For a more in-depth look at encryption, CompTIA Security+ is a safe bet, as it's entry level and vendor neutral
How Does Symmetric Encryption Work?
Symmetric, of course, means that something is the same on both sides. A symmetric key is one that is used by both the sender and the receiver of the message. Symmetric encryption gives the participants a level of privacy that they wouldn't get by sending a plaintext message that anyone could read.
Symmetric encryption uses a single key for both encryption and decryption of data. For symmetric encryption to work, both sender and receiver need to have a copy of the same key. There are several methods for sharing a symmetric key. One way is with a key agreement protocol.
The Diffie-Hellman key exchange method was developed in 1976, and it involves a series of data exchanges — until an agreed-upon encryption key is determined. The Elliptic Curve Diffie-Hellman Ephemeral (ECDH) is an improvement on Diffie-Hellman, in that it makes use of complicated elliptical-curve cryptography.
With symmetric encryption, early developers had a choice for message delivery. They could send a continuous stream of data, or they could break up the data into defined segments. The result was the development of two different methods for encrypted data transfer.
Stream cipher is used in symmetric encryption to transmit one bit at a time, but it's not used as much these days. Block ciphers encrypt and send data in small sections, such as 64 bits, 128 bits, or 256 bits. Block ciphers include DES, Triple DES, RC5, and AES.
Stream cipher. A stream cipher is helpful when the potential length of the data transmission is uncertain. RC4, for example, is a stream cipher that generates a stream of bits — sent one bit at a time — that combines encryption with the plaintext message. It was used in early wireless security technologies like wireless LAN (WLAN). RC4 is simple and fast, although not considered so secure these days.
Block cipher. Block cipher segments the information into blocks of predetermined length. It was used in the popular Digital Encryption Standard (DES) algorithm in the 1990s. At first, it was commonly used. However, due to its 56-bit key length, people began to question whether they could trust block cipher.
Another name for symmetric key encryption is private key encryption. It's simple compared to asymmetric encryption, but it has its drawbacks. The biggest obstacle is getting the key to the person with whom you are sharing data.
And sending a private key over the internet is a problem. What if someone else gets hold of it? There is a better alternative.
How Does Asymmetric Encryption Work?
Asymmetric keys are different, but related in such a way that they can function together. The two keys are not handled the same, however. The website granting access creates both a public key and a private key. They keep the private key and send the public key to the potential user. Using the public key, a user can send an encrypted message to the receiving website.
When the sender types their message, it is in plain text. Before it hits the public internet, the message is encrypted so that no one else can read it. The receiver of the message can then use the associated private key to decipher the message back into plain text.
Because the public and private keys were issued together, they both are able to handle the message encryption and decryption. Here is an illustration of how this works.
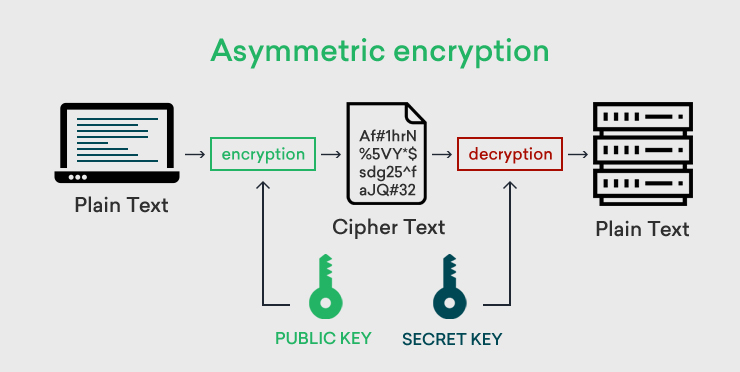
[Source: ClickSSL]
Asymmetric key encryption is also called public key encryption, and it's part of the public key infrastructure (PKI). But asymmetric keys come with problems of their own. Because the public keys are generally available to anyone, how can you verify whether the message encrypted and sent to the website is actually valid?
To provide even more security, public encryption often involves the use of a digital signature. This is a method for verifying the identity of the sender and confirming the integrity of the message.
Symmetric or Asymmetric: Which is Faster?
Symmetric encryption is faster than asymmetric encryption because it only uses one encryption key. With every added layer of encrypted security, the speed of the data transmission inevitably decreases. That's because it takes more processing time to encrypt and decrypt the messages. The more complex the encryption, the slower the data transmission.
Symmetric or Asymmetric: Which Is More Secure?
The answer to this question depends on the encryption algorithm used and the number of keys in the algorithm. But generally speaking, asymmetric encryption is considered more secure because it requires two keys rather than just one.
As you will learn while preparing for certification exams like CompTIA Security+, the asymmetric key pair requires more mathematical computations to set up the handshake between the two parties. And with asymmetric encryption, the receiver of the transmissions keeps the private key and does not share it with anyone.
When to Use Symmetric Encryption
Symmetric encryption is used when speed and performance are the primary issues. For this reason, it is the encryption of choice when dealing with large amounts of data. Bulk encryption may be involved in the processing of payment applications, for instance, or in the generation of random numbers.
Large-scale symmetric encryption systems can be a challenge, especially when handling transmissions over large geographical distances. The use of centralized key management software is another factor to consider when initiating symmetric encryption.
When to Use Asymmetric Encryption
When you create a secure connection over an insecure network, asymmetric encryption is the way to go. As part of the Public Key Infrastructure (PKI), asymmetric keys, as well as digital certificates, are issued by certificate authorities (CA). One of the most common uses of asymmetric encryption is the creation of secure websites using either SSL or TLS protocols.
Any time you see a website that has HTTPS in the URL rather than HTTP, you are looking at a page that has been secured with SSL/TLS. Other common uses of asymmetric encryption are digital signatures and cryptocurrency (such as Bitcoin).
When to Use Hybrid Encryption
Another option is to use both symmetric and asymmetric encryption in the same solution. The way this works is that the sender uses asymmetric encryption to encrypt both the message and a symmetric key that they transmit to the receiver. The receiver then uses their public key to decrypt the message as well as the symmetric key. With a fresh symmetric key, the receiver can then send secure messages, knowing that no one else could possibly have the symmetric key.
Final Thoughts
CompTIA's Security+ exam is a great way to validate your understanding of encryption technologies. Symmetric encryption is an old standby, and it's not as commonly used now as asymmetric encryption. But when you want to securely send large amounts of data, you can't beat symmetric encryption for speed, efficiency, and performance.
Asymmetric encryption, on the other hand, uses a pair of encryption keys generated by a certificate authority. The complexity of asymmetric encryption makes it both more secure and generally slower. A hybrid approach combines both technologies in a single solution.
delivered to your inbox.
By submitting this form you agree to receive marketing emails from CBT Nuggets and that you have read, understood and are able to consent to our privacy policy.